Strengthening organizational resilience
Everbridge provides a single hub for incident preparedness, risk monitoring, critical event management, and service reliability.

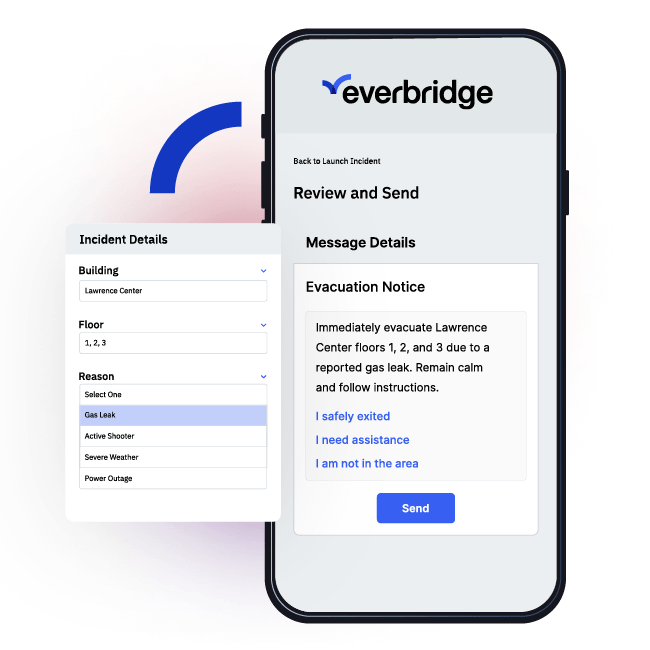
We enable customers to navigate the unpredictable world more safely, protect revenue, and minimize operational and recovery costs when critical events occur.
Everbridge provides a single hub for incident preparedness, risk monitoring, critical event management, and service reliability.
Proactively identify, assess, and monitor risk
Respond instantly and accurately to every incident
Safeguard digital and physical assets
Keep your people safe and productive
Anticipate and mitigate the impact of disruptions to strengthen
business continuity.

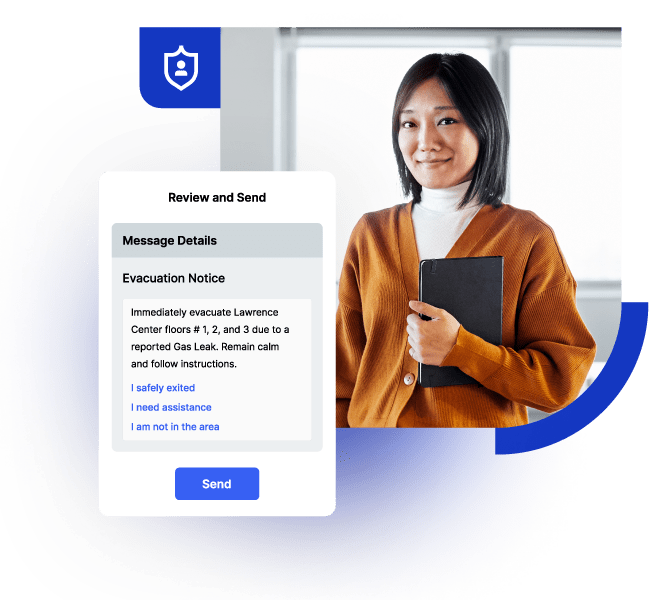
Maximize workforce safety, well-being, and productivity wherever people are.
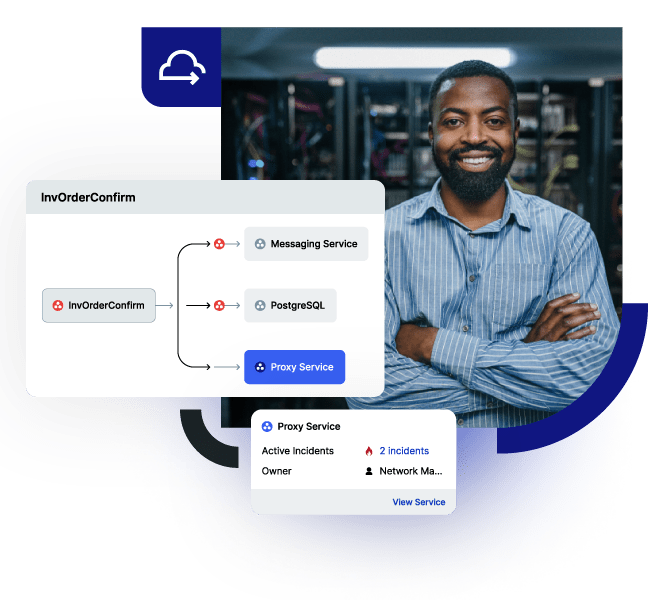
Minimize the impact of IT service disruptions and reduce
unplanned work.
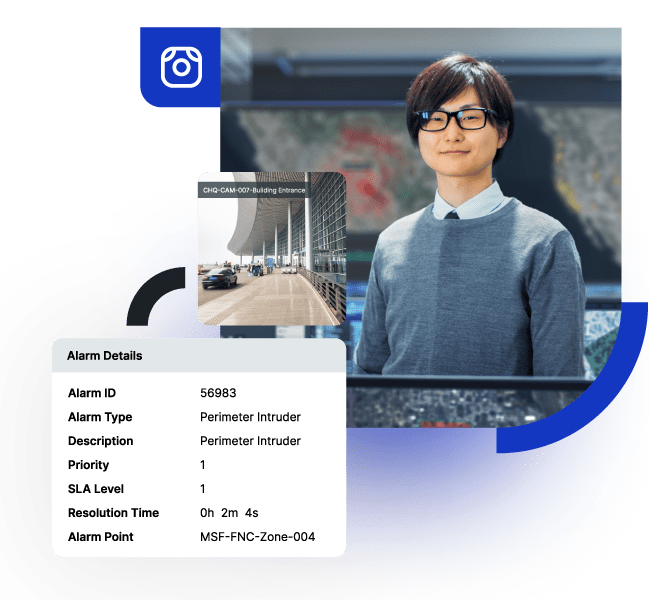
Protect buildings, assets, and people in your physical locations.
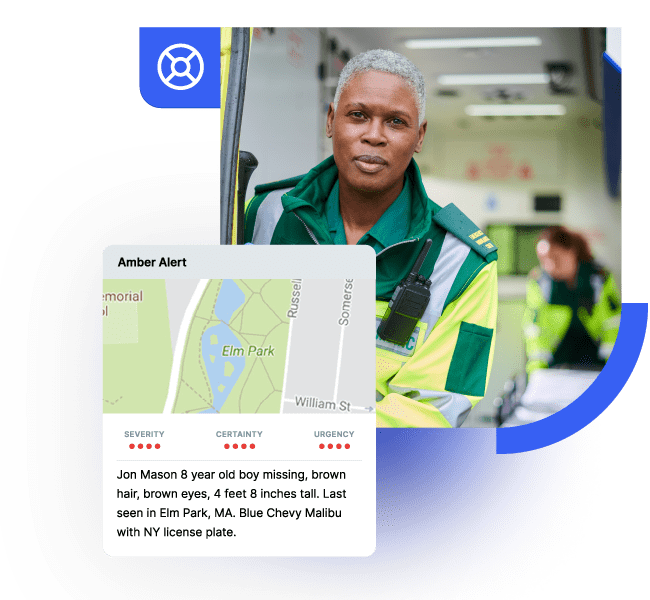
Safeguard the public before, during, and after critical events.
6,500+ global customers
6.9 billion interactions
1,800+ global employees
Serving more municipalities, states and countries than any other provider